We live in a world, which is slowing but strongly connecting through the network. From social media to business transactions & government plans, all are interconnected. Protecting those vital business information or we can say the entire connected network is not optional, it’s extremely important.
Our global economy heavily relies on data and information carried through cyberspace. It is our sole responsibility to take care of our property from potential theft, hackers or even competitors. If you remember, in between 2013 to 2015, many high profile companies in the US particularly complained that their internal information has been leaked & much data has been hacked. The cyber-attack on Sony highlighted matter and afterwards many US business organisations started evaluating their IT infrastructure.
Cyber Security for Business
There are much sensitive information in your business. Such as passwords, financial details, security numbers, emails, employee details, source code, client details, database, quotations or any information which is critical to your financials as well as business success. Network security is the foremost important thing for any organisation.
There are many steps business takes to protect themselves from cyber-attacks. IT team employs physical and software security at various layers in the infrastructure like Application, Network, Server, and Machine. Organisations train employees like never click on any links in an unknown email, never open attachments from unknown senders, never share personal information, change passwords often, protect office Wi-Fi with a password, and protect machines with passwords and much more.
A study on data security in 2011 says, more than 80% of the data leaked from the organisation because of internal negligence
Hackers are hard. They always try to find a way to crack your security protection. If you are not keeping yourself a step ahead towards your internal data protection, there is a bigger chance that it might badly damage your brand value. Don’t take chances, when it comes to any kind security.
Apogaeis is here to help you in protecting your company network, owned software, custom web application and database from any kind of security attack. You need think and act like a hacker to protect information. It is not a newbie job.
Cyber Security for Customers
Your business enterprise’s success largely depends on your customer base and relationship with them. Your customers want you to provide them excellent service and address their concerns immediately. If you fail, within no time they will switch.
With the evolution of social media, the information sharing between service provider & customers are happening largely online. A huge amount of customer information is been transferred and stored digitally on an everyday basis. Don’t you think there are many hackers who always look for numerous ways to steal such important customer data? These can be your customer’s contact details, credit card details, bank account details, email id credentials, confidential source code and much more. If any customer’s information is misused because of your network security failure, you can imagine the consequences. They might take legal actions against you as well as they can use social media to destroy your brand value.
It is essential to invest on cyber-security to avoid any kind network security failure. Apogaeis helps its clients to setup entire infrastructure by identifying weak links in networks to ensure data safety.
According to a report published in Jan 2015 on Global risks by the World Economic Forum (WEF), “90 percent of companies worldwide recognise they are insufficiently prepared to protect their information against cyber-attacks.”
Business leaders, European & US governments are very much aware and continuously try to find ways to counter cyber crimes. They invest heavily on cyber defence strategies and technical innovations. Many conferences and summits are happening around the globe to discuss cyber crimes and ways to fight against it. In the end of 2014, a cyber security conference held by “The European Network & Information Security” witnessed participation of 29 countries and over 200 organisations, including government bodies, telecom giants, E-commerce players, top financial firms, energy & power suppliers etc.
In February 2015, US President Barack Obama addressed a Summit on “Cyber security and Consumer Protection at Stanford University”. Many senior US political leaders, CEOs and board of directors from computer security companies, major retailers, telecom service providers, and technical experts participated to collaborate and work together in the way to develop & implement best strategies to strengthen cyber security.
To competently perform rectifying security service, two critical incident response elements are necessary: information and organisation.
Robert E. Davis
The Rise of Vulnerability
The security threat is rising only because data available online. Technical developments and new innovations are helping but these innovations are also a part of these threats.
How to counter cyber risks?
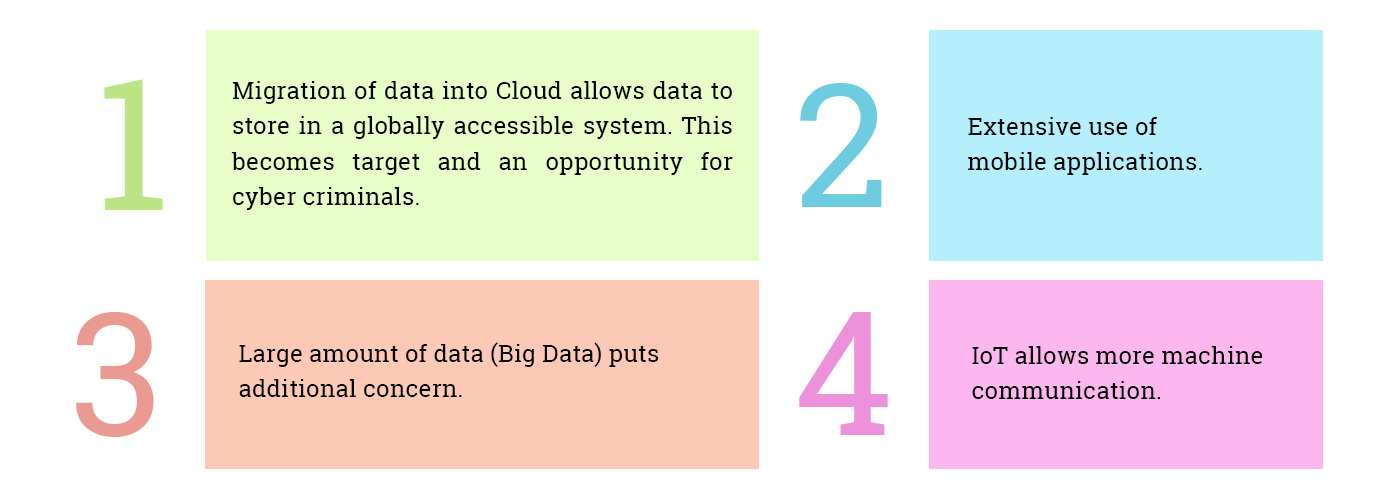 What organisation need to do is build effective cyber security solutions to monitor & control real time flow of inside/outside data flow, business process, systems, database, networks, business applications and customer information. This is exactly what Apogaeis’s cyber security solutions are based on.
What organisation need to do is build effective cyber security solutions to monitor & control real time flow of inside/outside data flow, business process, systems, database, networks, business applications and customer information. This is exactly what Apogaeis’s cyber security solutions are based on.
The first step is to identify the security risks and strategies for dealing with them. By adopting standard security measures you should disable functions which are not required and keep security locks on other functions.
- Malware Protection: Regular malware scanning of systems, limited use of personal devices, email policies, web policies are very important for data security.
- Network Protection: Network protection is very important, as it can a weak link. It is crucial to follow proper network design principles and ensure all the connected systems are configured according to the security standards.
- Application Security: Application Security Architecture must be thought well at the early stage of SDLC. Optimum security implementation helps to identify and fix any critical vulnerability before it is too late. Application security testing, Open source software analysis, web application firewall, service protection are the focus areas. It costs less in long run.
- Identity and Access Management: As your business expands, you connect with more and more vendors, partners, and customers. At the same time, the identity and access management becomes a challenge. With the advancement of BYOD, IoT and M2M communication, organizations are more protective in managing their business information. IAM should be the first line of cyber defence.
Let’s talk about challenges and scope of cyber protections.
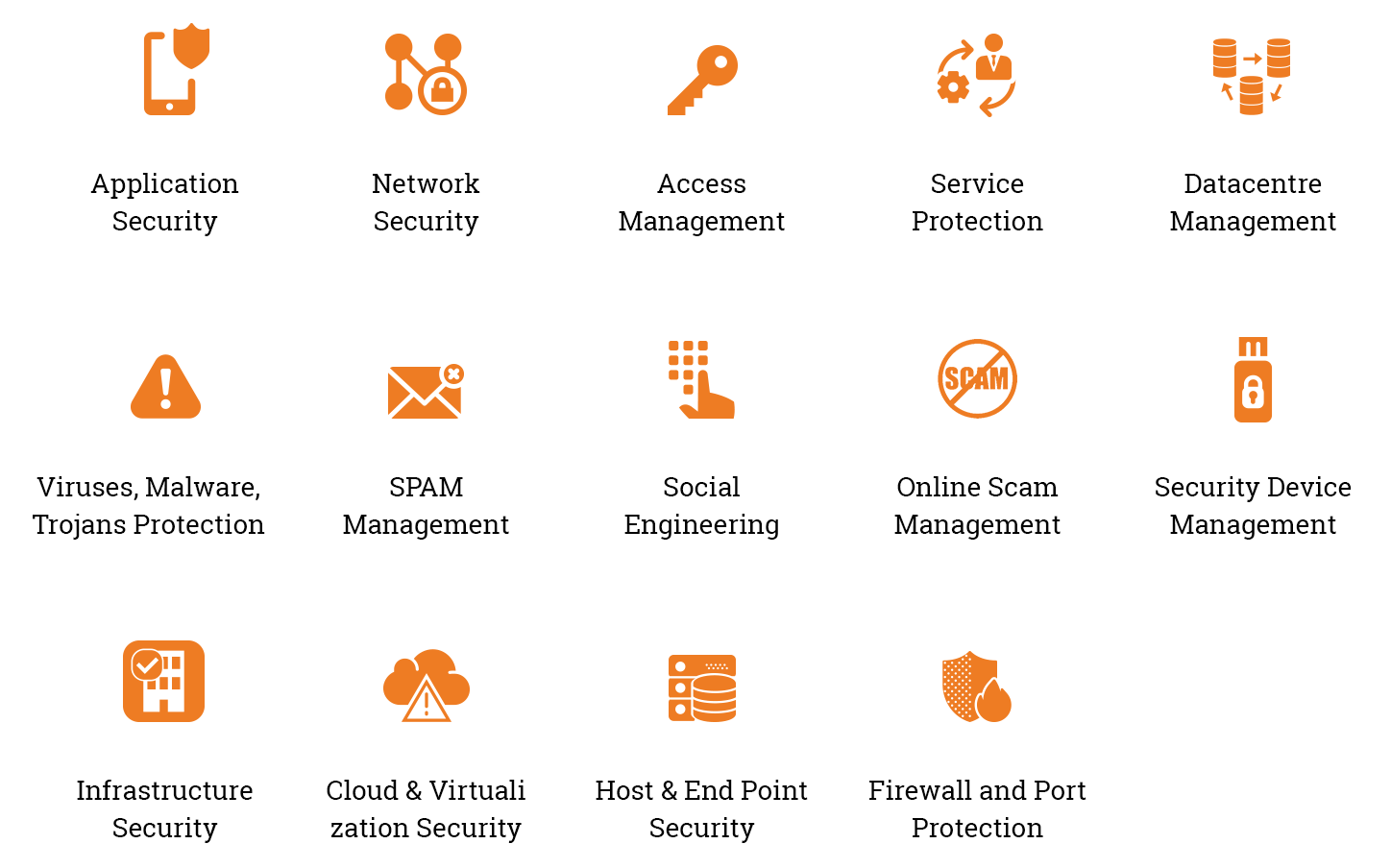
Beside these, Information Security Policies should be added in employee NDA at the time of joining & regular training should be provided for internal safety. All the machines used inside the work premises should be tracked, monitored and inspected on regular basis. Inflow and outflow of data should be monitored and filtered.
Conclusion
Cyber security is a global threat. It should be managed strategically at all the levels in an organisation, from an individual perspective to the in-house IT department. Networks are been the target of cyber criminals and will continue. There are precautions which organisations can take internally, as well as they need to consult expert cyber security solutions providers. There is no silver bullet cyber security solution, a layered defence is the only solution. With the proper monitoring and specialist assistance, it is possible to protect business and personal information.
Apogaeis is a specialist cyber security consulting firm and a solution provider. We streamline your current software solutions, mobile applications, web applications, and set up data backup. We do work on recovery strategies, remote network controlling solutions, technology consulting, application development, product management and IT solutions. We have the expertise to offer the security of information assets, structured risk assessment, applications security services, data encryption services and much more. Find out more information at https://www.apogaeis.com/innovation/
Click Here to talk to our consultant to understand more on how to protect your network.










